Logging into a live server is inherently risky. You could do anything: take down a service, wipe your customer data, or trash the Operating System. There’s no undo.
Whatever you do:
- Back up your site files and databases and enable full server backups at your provider.
- No really. Go back to step 1 and double-check.
- Consider safer access methods before SSH.
- Restrict SSH access to essential users only.
- Understand the implications of every command you enter.
- Know how to revert when catastrophe occurs. A backup is only of use if you can restore the data.
Alternative Access Methods
Depending on your SSH experience level, you may be more comfortable managing aspects of your server through other means:
- The WordPress dashboard allows you to configure many aspects of your WordPress site. You can even edit PHP theme source files.
- Database clients provide a web or native app access so you can examine and modify data.
- Version control repositories such as GitHub and Bitbucket can deploy source code updates.
Remote Login via SSH
SSH (Secure Shell) is an open protocol that allows you to securely connect to a remote server and execute commands or transfer files. A shell is a user interface that gives you access to an Operating System through a command line where you type instructions at a prompt.
SSH has advantages over older protocols such as telnet and FTP (File Transfer Protocol):
- It uses public key data encryption: third parties cannot eavesdrop, tamper, or spoof messages.
- Authentication. SSH provides more ways to permit and block user access
- Data integrity. SSH uses hashing to ensure data is not altered when transmitted between the client and server.
- It supports advanced networking features such as tunneling, port forwarding, and proxying.
SSH is ubiquitous. If you can use it in one place, you can use it anywhere – although be aware there may be differences when you access the OS of the remote machine.
Before we can experiment with SSH, we need a server we can connect to via SSH. If you have an extra computer laying around, you could set it up with Ubuntu, or you could set up a virtual machine on your local computer with Ubuntu Multipass or similar software, but by far the quickest and easiest way to set up a remote server is to create a cloud server. Let’s provision one at Vultr.com.
Provisioning a Vultr Server
If you don’t already have a Vultr account, you can register at https://www.vultr.com/register/. (New to Vultr? Sign up with our special link and receive $100 in Vultr credits.)
You can provision a new server from your Vultr dashboard by clicking Deploy + in the upper right and then selecting Deploy new Server.
You will need to select from a number of options for the new server. For the sake of this tutorial, we can provision a small server with minimal available resources to keep things affordable.
For Choose Server, select Cloud Compute.
CPU & Storage Technology should be AMD High Performance
Select any Server Location you like. Whatever is nearest to you should prove to be the quickest response times.
For Server Image, select the most recent LTS release of Ubuntu. At the time of writing, that’s Ubuntu 22.04.
Server Size should be 25GB NVMe, the smallest and cheapest option available.
We’ll only be needing this server short term to experiment on, so you can safely turn off Auto Backups.
Under Additional Features, you should need only Enable IPv6.
Next, we’ll see the SSH Keys section. We will be adding an SSH key later in this tutorial but we’re not there just yet. You can skip this section.
Finally, you can enter a Server Hostname. This can be any name you like.
Click to finalize things and the provision process will start. This can take a few minutes to complete.
Once the provision process completes, you can view the dashboard for the new server to find the IP address and root password you will need in order to connect to the server using SSH.
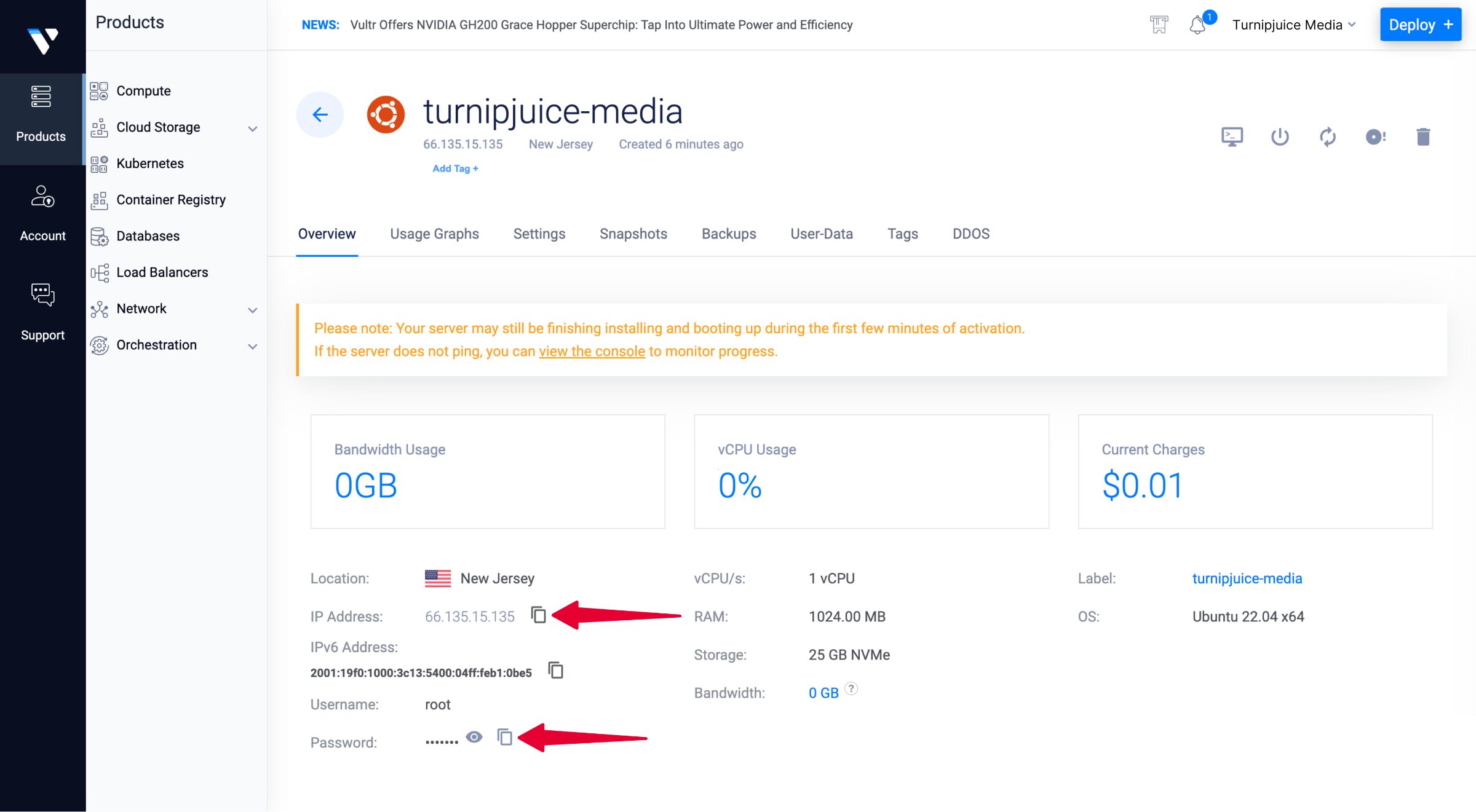
Install and Enable SSH Administration (Skip if using Vultr)
Most cloud server providers, including Vultr, install and configure SSH on their servers by default, so you don’t have to do it. However, if you’ve set up your own machine or virtual machine, it might not have SSH installed. You may need to install OpenSSH to allow users to connect via an SSH client on the default HTTP port 22. Installation instructions vary but, on Ubuntu/Debian flavors of Linux, it’s:
sudo apt install openssh-serverYou may need to edit the configuration file at /etc/ssh/sshd_config to allow access permissions to specific users, e.g.
PermitRootLogin no
AllowUsers abe jane keith lenathen restart the service:
sudo systemctl restart sshOn Windows, you can install OpenSSH Server from Windows Settings > Apps > Optional Features, then clicking Add an optional feature.
Make a note of:
- your server’s public IP address and/or hostname, and
- your account ID and password.
Client Software Requirements
Open a command line shell on your computer. Linux and macOS users will find an application named Terminal or similar. Windows users can use Powershell or Command Prompt, but it’s best to install Windows Terminal which can manage any shell.
To connect to your remote server, you require SSH client software. Linux distros, macOS, and Windows 10+ provide a built-in SSH client. To check it’s installed, type ssh at the command prompt and you should see usage instructions such as:
$ ssh
usage: ssh [-xxxxxxxxxxxxxxxxxxxxxx] [-B bind_interface]
[-b bind_address] [-c cipher_spec] [-D [bind_address:]port]
[-E log_file] [-e escape_char] [-F configfile] [-I pkcs11]
[-i identity_file] [-J [user@]host[:port]] [-L address]
[-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port]
[-Q query_option] [-R address] [-S ctl_path] [-W host:port]
[-w local_tun[:remote_tun]] destination [command]If you’re on Linux and see:
ssh: command not foundinstall the OpenSSH client for your distro. On Ubuntu or Debian:
sudo apt install openssh-clientUsers of older editions of Windows may see the following error message:
'ssh' is not recognized as an internal or external commandConsider installing software such as Putty to manage remote logins.
Log in for the First Time
Log into your remote server by entering the command ssh <user>@<remote-address> using your SSH credentials:
<user>is your user ID on the remote machine, and<remote-address>is the remote server’s IP address or hostname
For example, if your user ID is abe and the remote IP is 172.16.33.4, you’d enter:
ssh [email protected]Following along with our Vultr example, we’ll be connecting using our root user.
On establishing an SSH connection, you will be asked if you’re sure you want to connect:
$ ssh [email protected]
The authenticity of host '172.16.33.4 (172.16.33.4)' can't be established.
ECDSA key fingerprint is ab:cd:ef:00:11:22:33:44:55:66:77:88:99:00:ab:cd.
Are you sure you want to continue connecting (yes/no)?Enter yes and you’ll see a prompt for your password on the remote server:
[email protected]'s password:Enter the correct password (you won’t be able to see password characters as they’re typed) and you should see something similar to the following:root@localhost:~$ ssh [email protected] Welcome to Ubuntu 22.04 LTS (GNU/Linux 5.15.0-41-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Tue Aug 30 18:48:33 UTC 2023 System load: 0.9072265625 Users logged in: 0 Usage of /: 6.3% of 24.05GB IPv4 address for eth0: 172.16.33.4 Memory usage: 23% IPv4 address for eth0: 10.20.0.11 Swap usage: 0% IPv4 address for eth1: 10.118.0.8 Processes: 99 0 updates can be applied immediately. The list of available updates is more than a week old. To check for new updates run: sudo apt update
Congratulations, you’ve logged in to a remote server for the first time! You now have full root access to the server. Every command you enter will execute on that machine — not your local computer.
For security reasons, we typically disable the ability to log in to a remote server with the root user, so the first thing we’ll do is add a new non-root user account to use for the rest of the tutorial. We’ll be making a user account for a user named abe. Once the abe user is created you should treat it as your default account as there are a few extra safety nets for non-root users making it harder to inadvertently break things.
To start the process, invoke the adduser command:
adduser abeYou will be prompted for some additional information. All information other than the password is optional and can be left blank.
Once the process completes and the user has been created, we can close the connection and reconnect using our new abe user.
Type exit to close the connection.
exitThis will close your connection to the remote server. Now you can open a new connection for the abe user.
ssh [email protected]Type ls to see a list of files and directories:
[email protected]:~$ ls
backups configs documents media web wp-content backup.sh
[email protected]:~$To close the connection, type exit.
Configuring Secure Passwordless Login
Using a password to log into a remote server is not secure and having to remember the correct password to use each time can be inconvenient.
SSH uses public-private key authentication, eliminating the need for a password to log into the remote server. While you can use either password authentication or public-private key authentication or even both with SSH, public-private key authentication is far more secure than password authentication and the route we strongly recommend taking.
SSH keys are a matching set of cryptographic public and private keys which you can use for authentication. Your private key remains on your computer and should never be distributed. You can share your public key with anyone or any system — such as the remote server you want to log into. When you attempt to connect from the client machine to the server, the SSH client uses the private key to create a signature that is sent to the server. If the public key on the server validates the signature, access is granted.
If you find the instructions below a hassle, you might want to try SpinupWP as it offers a convenient UI for adding system users and adding SSH keys to those users.
To create a key pair, enter the following command in your computer’s terminal (not the remote server):
ssh-keygen -C "<name-or-email>" -t rsaWhere -C "<name-or-email>" is an optional name or email address, e.g.
ssh-keygen -t rsa -b 4096 -C "[email protected]"The prompt will ask you to confirm where to save the keys — press Return to accept the default location:
Generating public/private rsa key pair.
Enter file in which to save the key (/home/abe/.ssh/id_rsa):The prompt will then ask for a passphrase. The passphrase must be entered every time the key is used so it’s a bit of an inconvenience but an extra layer of security in case anyone gets access to that private key on your machine. It’s up to you, but if you prefer the convenience just hit Return for no passphrase:
Enter passphrase (empty for no passphrase):
Enter same passphrase again:Your identification has been saved in /home/abe/.ssh/id_rsa.
Your public key has been saved in /home/abe/.ssh/id_rsa.pub.
The key fingerprint is:
ab:cd:ef:00:11:22:33:44:55:66:77:88:99:00:ab:cd abe@bobspc
The key's randomart image is:
+--[ RSA 2048]----+
| |
| |
| |
| - + |
| + o . |
| S . * + |
| S + = * - |
| + o = + |
| ...+B=+ |
+-----------------+Two files are generated in the local .ssh directory shown:
id_rsa: the PRIVATE SSH key which you should keep safe and never distributeid_rsa.pub: the public SSH key you can safely share.
Add your private keys to an SSH Agent so it’s used whenever you log onto a remote server:
On Linux only, you must start the SSH Agent with:
eval $(ssh-agent)Add the key (on any device) using ssh-add followed by the path of the private key:
ssh-add /home/abe/.ssh/id_rsaNow you can return to your Ubuntu server and add this information to get things authorized. You can append the content of your public id_rsa.pub file to the authorized_keys file belonging to your abe user. This file can be found at ~/.ssh/authorized_keys file. The easiest option is the ssh-copy-id command supplied with some Linux distros:
ssh-copy-id [email protected]
If this is not available, log on as before, and create an authorized_keys file:
mkdir -p ~/.ssh
cd ~/.ssh
touch authorized_keysOpen your computer’s id_rsa.pub file in a text editor (see our How to Easily Edit Files Over SSH with Nano tutorial for step by step instructions) and copy the whole line using Ctrl | Cmd + C. It’s a long string of random hex digits with the name/email address at the end (if provided):
ssh-rsa ABC...etc...== [email protected]Append this string to ~/.ssh/authorized_keys by pasting it into the following command on the remote server using Ctrl | Cmd + V:
echo <paste-here> >> ~/.ssh/authorized_keyse.g.
echo ssh-rsa ABC...etc...== [email protected] >> ~/.ssh/authorized_keysCheck the content of the updated file to ensure the key was added:
$ more ~/.ssh/authorized_keys
ssh-rsa ABC...etc...== [email protected]Exit the remote server by entering exit then log in again (ssh [email protected]) — you shouldn’t be prompted for a password.
Navigating the Shell
This section provides a list of useful commands and options you can enter when connected to your remote server. In most cases, it’s likely to be a Linux box running bash (Bourne-Again SHell). If a command fails, you’re possibly using a different shell, so consult your web host or OS documentation.
Command Help
In most cases, you can add --help to any command to see help, e.g. for help on the ls command:
ls --helpSome commands have a lot of options so it’s easier to use man followed by the command:
man lsYou can navigate man pages using arrow keys, and exit back to the shell at any time by pressing q.
In most cases, Ctrl | Cmd + C stops a command running.
To clear the screen, enter clear or press Ctrl | Cmd + L.
Move Around Directories
All Linux directories start at the / root. A forward slash denotes a sub-directory. Important server paths and locations, include:
/home/– contains personal files for all users, such as/home/abe/and/home/jane//etc/– typically contains application configuration files/var/www/html/– typically contains NGINX web server files/var/log/– contains logs for lots of different applications each in their own folder
You can navigate around directories using the cd (change directory) command. You’ll typically start in your /home/<username>/ directory and can move into a subdirectory named wp-content (where WordPress stores theme and plugin files) using:
cd wp-contentor
cd ./wp-contentwhere the initial period . denotes the current directory.
You can also specify the full path from the root:
cd /home/abe/wp-contentTo move out of the wp-content directory back to /home/abe/, enter:
cd ..You can also return to your home directory from anywhere using:
cd ~Listing Files
List the content of any directory using ls to show the files and subdirectories, e.g.
$ cd ~
$ ls
backups configs documents media web wp-content backup.sh
$ cd wp-content
$ ls
languages plugins themes uploads index.phpYou can list the content of any directory without moving from the current one. For example, to see what’s in /etc/:
ls /etc/Add -l to show file details in a longer format, e.g.
$ cd ~
$ ls -l
drwxr-xr-x 2 abe abe 4096 Jun 22 10:49 backups
-rwxr-xr-x 2 abe abe 4096 Jun 22 10:49 backup.sh
drwxr-xr-x 2 abe abe 4096 Apr 12 09:23 configs
drwxr-xr-x 2 abe abe 4096 Sep 05 02:55 documents
drwxr-xr-x 2 abe abe 4096 Jun 15 00:12 media
drwxr-xr-x 2 abe abe 4096 Feb 09 07:30 web
drwxr-xr-x 2 abe abe 4096 Jan 31 09:01 wp-contentHidden files and directories such as .ssh are not shown by default, but you can see them by adding -a. Optionally, you can combine this with -l, e.g.
$ cd ~
$ ls -la
drwxr-xr-x 2 abe abe 4096 Jun 22 10:49 backups
-rwxr-xr-x 2 abe abe 4096 Jun 22 10:49 backup.sh
drwx------ 2 abe abe 4096 Jun 21 18:02 .bash_history
drwx------ 2 abe abe 4096 Jun 21 18:02 .bash_logout
drwx------ 2 abe abe 4096 Jun 21 18:02 .bashrc
drwxr-xr-x 2 abe abe 4096 Apr 12 09:23 configs
drwxr-xr-x 2 abe abe 4096 Sep 05 02:55 documents
drwx------ 2 abe abe 4096 Jun 21 18:02 .local
drwxr-xr-x 2 abe abe 4096 Jun 15 00:12 media
drwx------ 2 abe abe 4096 Jun 21 18:43 .ssh
drwxr-xr-x 2 abe abe 4096 Feb 09 07:30 web
drwxr-xr-x 2 abe abe 4096 Jan 31 09:01 wp-contentViewing Files
You can view the full content of files using the cat or more commands. This can be useful for WordPress or other debugging. For example, to view the NGINX access logs:
$ more /var/log/nginx/access.log
11.22.33.44 - - [06/Oct/2023:01:04:31 +0100] "GET / HTTP/1.1" 401 179 "-" "-"
44.33.22.11 - - [06/Oct/2023:01:04:31 +0100] "GET / HTTP/1.1" 401 179 "-" "-"A --More-- prompt is shown at every screen full. Press any key or Q to quit.
The tail command shows the last 10 lines of a file which can be useful for logs. You can show more lines with -n <lines>, e.g.
$ tail /var/log/nginx/access.log -n 20The -f (follow) option keeps tail running and outputs further lines as they are appended:
$ tail /var/log/nginx/access.log -fPress Ctrl | Cmd + C to exit. This is really handy when you want to watch a log file for new entries.
Creating Files and Directories
Create a new empty file in the current directory using touch followed by a name:
touch newfile.txtCreate a new subdirectory in the current directory with mkdir followed by a name:
mkdir newdirectoryYou can create deeply nested directories using the -p option:
mkdir -p /home/abe/newdir1/sub/subsub/subsubsubDeleting Files and Directories
Delete files in the current directory using rm followed by a name:
rm newfile.txtYou can also use wildcards, for example to delete every .txt file:
rm *.txtTread very carefully when working with wildcards in rm commands as it’s very easy to permanently delete more files than you intended to. There is no Trash you can restore deleted files from like on macOS or Windows.
Delete a directory rmdir followed by a name:
rmdir mydirectoryThis will fail if the directory contains files or sub-directories. You can force it to delete everything recursively by adding -rf – so be careful what you’re doing! It’s easy to delete whole directories of important files.
rmdir -rf mydirectoryMoving and Copying Files
Copy files and directories from one place to another using cp followed by the source and destination. For example, to make a backup of the NGINX access log to your ~/backup/ directory:
cp -p /var/log/nginx/access.log ~/backup/You can recursively backup the whole /var/log/nginx/ directory including all files and subdirectories with the -r option:
cp -rp /var/log/nginx/* ~/backup/Moving files with mv is similar to cp. For example, to move ~/backup/ to ~/mybackups/:
mv ~/backup/ ~/mybackups/Viewing Server Information
You can see how long a server has been running using uptime:
$ uptime
15:40:11 up 10 days, 20:53, 1 user, load average: 0.00, 0.00, 0.00The top command shows a (long) live list of processes and CPU activity:
$ top
Tasks: 139 total, 1 running, 138 sleeping, 0 stopped, 0 zombie
%Cpu(s): 0.1 us, 0.3 sy, 0.0 ni, 99.6 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
MiB Mem : 909.6 total, 322.3 free, 93.7 used, 493.6 buff/cache
MiB Swap: 100.0 total, 100.0 free, 0.0 used. 752.7 avail Mem
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
63400 abe 20 0 9860 3260 2724 R 1.0 0.3 0:00.16 top
63313 root 20 0 0 0 0 I 0.7 0.0 0:09.10 kworker/2:2-events
407 message+ 20 0 8156 3804 3260 S 0.3 0.4 7:02.93 dbus-daemon
1 root 20 0 165224 10188 7444 S 0.0 1.1 0:32.74 systemd
2 root 20 0 0 0 0 S 0.0 0.0 0:01.82 kthreadd
3 root 0 -20 0 0 0 I 0.0 0.0 0:00.00 rcu_gp
4 root 0 -20 0 0 0 I 0.0 0.0 0:00.00 rcu_par_gp
5 root 0 -20 0 0 0 I 0.0 0.0 0:00.00 slub_flushwq
6 root 0 -20 0 0 0 I 0.0 0.0 0:00.00 netnsPress Q to quit.
A human-readable summary of disk space used by a folder and its contents can be achieved with the following command:
$ du -sh
54M .To see the space available on various mounted filesystems you can use the df command:
df -h
Filesystem Size Used Avail Use% Mounted on
/dev/sdc 251G 17G 222G 7% /
rootfs 7.7G 1.9M 7.7G 1% /initTransferring Files to and from the Remote Server
The scp command allows you to copy files or directories to and from your remote server.
To copy myfile.txt from your computer to /home/abe/ on the remote server at `172.16.33.4“, enter the following command in your local computer’s terminal (not the remote server shell):
scp myfile.txt [email protected]:/home/abe/Recursively copy a whole directory and all subdirectories using the -r option:
scp -r mydirectory [email protected]:/home/abe/Switching the source and destination around downloads files from the remote server:
scp -r [email protected]:/home/abe/mydirectory ./mydirectory-copyWhile file transfer is possible from the command line, it’s often easier to use a dedicated file transfer application such as FileZilla. This supports SSH and key-based authentication.
Quick Commands and Keyboard Shortcuts
The following shortcuts can help reduce typing effort. Variations may occur across systems.
| shortcut | function |
|---|---|
Ctrl | Cmd + L | clear screen |
Tab | autocomplete path/file name |
Ctrl | Cmd + S | stops output to screen |
Right cursor or Ctrl | Cmd + F | move cursor forward one character |
Left cursor or Ctrl | Cmd + B | move cursor back one character |
Alt + F | move cursor forward one word |
Alt + B | move cursor back one word |
Ctrl | Cmd + A | move cursor to start of line |
Ctrl | Cmd + E | move cursor to end of line |
Ctrl | Cmd + D | deletes character under cursor |
Ctrl | Cmd + U | deletes from start of line to cursor |
Ctrl | Cmd + K | deletes from cursor to end of line |
Ctrl | Cmd + W | deletes command/argument before cursor |
Alt + . | uses last argument of previous command |
Up cursor or Ctrl | Cmd + P | previous command in history |
Down cursor or Ctrl | Cmd + N | next command in history |
Alt + < | first command in history |
Alt + > | last command in history |
Ctrl | Cmd + R | search history |
Ctrl | Cmd + J | end search history |
Ctrl | Cmd + G | exit search mode |
Ctrl | Cmd + Z | suspend current command and moves it to a background task |
Ctrl | Cmd + Q | resumes a suspended command |
!! | run last command |
!x | run last command that started with x |
Ctrl | Cmd + D | close session/terminal |
Want to be notified when this list of shortcuts is updated? Subscribe at the bottom of this page to get an email when this article is updated and to receive the latest news, updates and optimizations in performance and security.
User Permissions and the Super User
Linux restricts users from running dangerous tasks such as installing applications, deleting logs, or editing configuration files. Only a super user (also known as root user) can run such actions, but you can temporarily elevate yourself to super user status with sudo (super user do) followed by a command. For example, to update the latest package lists and install application upgrades:
sudo apt update
sudo apt upgradeOmitting sudo shows a “Permission denied” or similar message. You can use sudo !! to repeat the command as the super user.
Sudo is a convenient and safe way to run privileged commands, but you still need to exercise caution when using it.
File Permissions and Ownerships
You sometimes need to access files and directories owned by another user on the system. (Other users could include a web server.)
The ls -l command below shows that abe owns:
- the
backupsdirectory – shown with adat the start of a line, and - the
backup.shscript file.
$ cd ~
$ ls -l
drwxr-xr-x 2 abe abe 4096 Jun 22 10:49 backups
-rwxr-xr-x 2 abe abe 4096 Jun 22 10:49 backup.shThe three groups of rwx denotes read, write, and execute permissions for:
- the user, or whoever owns the files (
abe):rwx - the user group (
abeis in his own group):r-x - everyone else:
r-x
Everyone is permitted to execute backup.sh but only abe can write to (edit) the file.
The chmod command can change user permissions. If Abe wants to allow anyone to read, write, or execute the file, he can run:
chmod 777 backup.sh777 sets permissions for the user, group, and everyone. Each digit is a decimal representation of three bits for read (+4), write (+2), and execute (+1). A value of 5 would therefore set read and execute, but not write. Granting such a broad access permission is rare and could lead to security breaches – only grant access to those who need it.
To make a script executable, you can also use +x, e.g.
chmod +x backup.shIn some circumstances, you may want to change the file/directory owner using chown (change ownership):
sudo chown -R {site_user}:{site_user} /home/abe/webfilesFor example:
sudo chown -R jane:jane /home/abe/webfilesEditing Files
It’s often useful to open files in a text editor to view the content or make quick changes. As always, remember to backup first. For example, to backup an NGINX configuration file at /etc/nginx/nginx.conf:
cp /etc/nginx/nginx.conf ~/backup/nginx.conf.001
Your server may have several editors installed, but nano is one of the easiest. It’s probably installed but, if not, you can do so with:
sudo apt install nanoStart the editor with nano followed by the name of the file you want to edit, e.g.
nano /etc/nginx/nginx.conf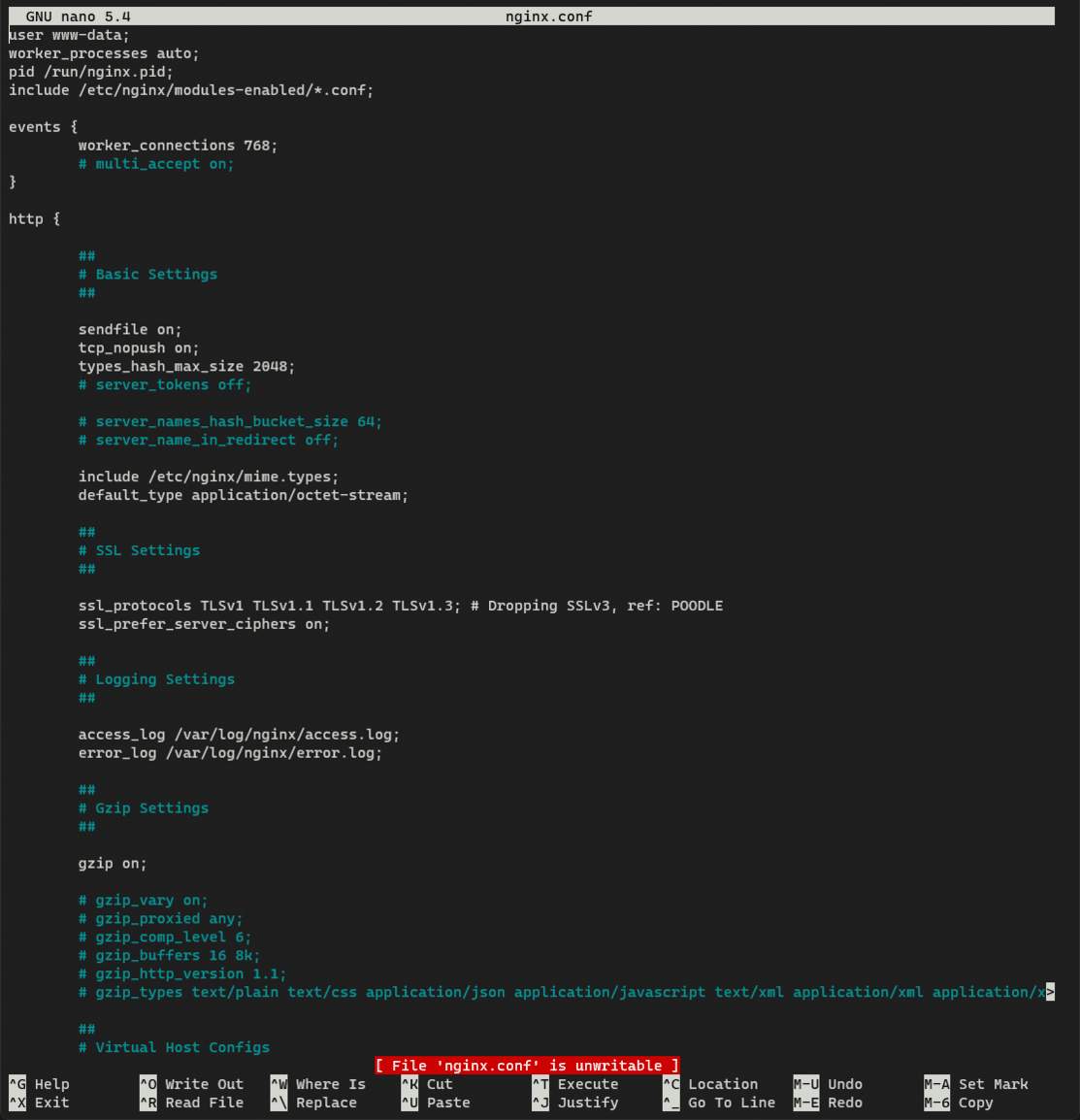
If you see a notice that the file is unwritable, you can exit by pressing Ctrl | Cmd + X then run sudo !! to reopen the file as a super user.
nano is not VS Code, but it’s good enough for quick and dirty editing. A concise keyboard shortcut guide is shown at the bottom of the screen, but the most important options are:
| shortcut | function |
|---|---|
Ctrl | Cmd + O | save (output) file |
Ctrl | Cmd + G | help |
Home or Ctrl | Cmd + A | move to beginning of line |
End or Ctrl | Cmd + E | move to end of line |
PageUp or Ctrl | Cmd + V | up one page |
PageDown or Ctrl | Cmd + Y | down one page |
Ctrl | Cmd + W | search |
Alt + W | find next match |
Ctrl | Cmd + \ | search and replace (supports regular expressions) |
Alt + A | set mark for selecting |
Alt + 6 | copy selected text |
Ctrl | Cmd + K | cut selected text |
Ctrl | Cmd + U | paste text |
Ctrl | Cmd + C | show cursor position |
Ctrl | Cmd + _ | go to line and column position |
Ctrl | Cmd + J | justify paragraph |
Ctrl | Cmd + T | spell check (if available) |
Ctrl | Cmd + R | open file and insert at current position |
Ctrl | Cmd + X | exit |
The following terminal text editors are available should you require more advanced functionality:
Writing Shell Scripts
Shell scripts are executable files containing one or more commands to complete a specific task. For example, say you want to back up a web uploads directory at /var/www/site/uploads/ and a MySQL database named website, you could create a file named /home/backup/backup.sh with those commands:
#!/bin/bash
# backup WordPress wp-content directory to a gzip file
tar -czf /home/abe/wp-content /home/abe/wpbackup.tar.gz
# backup database
mysqldump -u dbuser -p dbpass website > /home/backup/sql/dbbackup.sqlThe #!/bin/bash at the top is known as a shebang which tells Linux this is a bash executable script. Before you can run it, you must mark it as executable using chmod as we saw above:
$ cd /home/backup
$ chmod +x ./backup.shYou no longer need to remember the backup commands and can execute this script at any time by running:
$ ./backup.shor by specifying the full path:
$ /home/backup/backup.shOf course, you still need to remember to manually log in and run the script. Fortunately, the OS can do the hard work for you using cron to schedule jobs. To run the backup script at 4:00am every day, enter the following command:
crontab -eAn editor (possibly nano) will open. Add the following line to the end:
0 4 * * * /home/backup/backup.shSave the file with Ctrl | Cmd + O and exit with Ctrl | Cmd + X.
Like other programming languages, shell scripts support comments:
# do somethingtext output:
echo "Hello world!"variables (reference with a preceding $ after they are defined):
message="Hello world!"
echo $messagearguments passed to a script:
echo "first argument : $1"
echo "second argument: $2"arrays:
myArray=('one' 'two' 'three')
numElements=${#myArray[@]}loops:
for ((i = 0 ; i < numElements ; i++)); do
echo "element $i is ${myArray[${i}]}"
doneconditions:
if [ -f "./myfile.txt" ]; then
echo "myfile.txt exists"
else
echo "myfile.txt does not exist"
fiand functions:
# define function
start() {
echo "script starting"
}
# call function
startShell scripting is no substitute for programming languages such as C++, Java, JavaScript, Python, Rust, or Go but it’s adequate for simple tasks.
Other SSH Software
If you’re not satisfied with your OS’s built-in terminal, there is plenty of alternative terminal software to choose from.
Free SFTP (Secure File Transfer Protocol) apps include:
Linux file managers often have SFTP support and can mount a remote folder like any local folder.
Finally, some editors have features or plugins which allow you to SSH into a remote server and edit files directly:
BiSSH BaSSH BoSSH
SSH is an essential skill for anyone who needs to configure or maintain a remote system. It can be daunting if you’re not used to the command line but you should be able to grasp the core concepts within a few hours.
SSH gives you ultimate power over a system. But you did complete a backup first? I may have recommended that once or twice!
What’s the biggest problem you run into when accessing a server via SSH? Let us know in the comments below.
